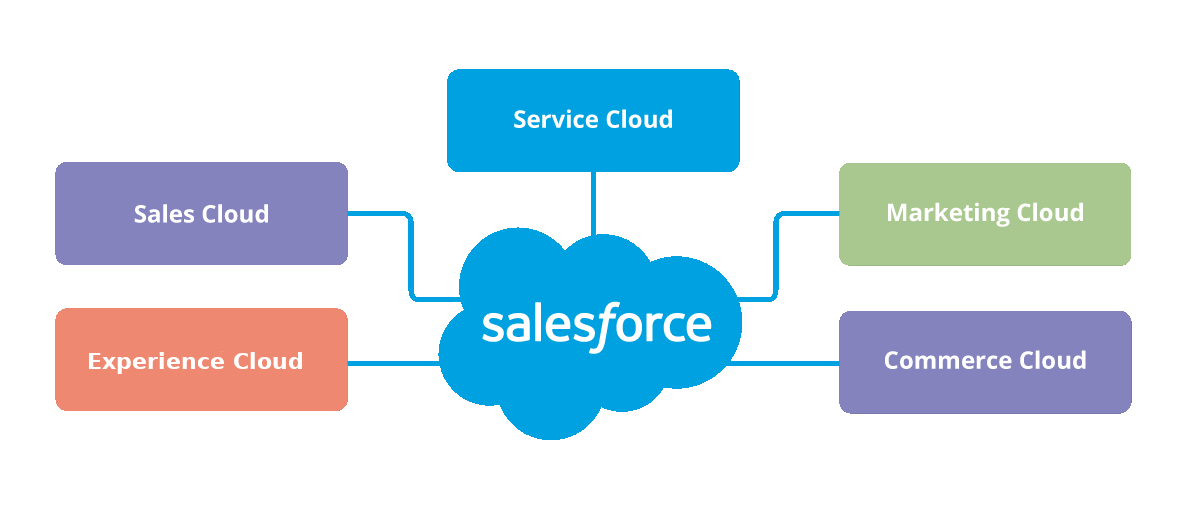
Salesforce is the world's #1 platform for customer relationship management but with high functionality comes complexity. We can help.


The ecosystem surrounding Google's products are second to none. We praise the platform's ease of administration and reliability. We can make your app vision reality.


$0
Get in Touch For A Free Quote
$90 /Hr
Salesforce and Google Development
